Recently, ransomware WannaCry has created ripples over the internet. The vulnerability in VLC-like streaming apps also came into light recently. There were other malware after WannaCry. All these malwares are limited to PCs. Now, Android smartphones are being affected with the new malware called Judy. The Judy malware is likely to affect forty one other apps available on PlayStore. After repeated request-to-removes, Google started removing all the apps infected by Judy. Nearly, 36.5 million Android devices - smartphones, tablets and phablets were likely to be infected by this malware.
In Google I/O 2017, Google has stated that globally two million devices are powered by Andoird. The attackers took the advantage of this number and started infecting the Android devices with the Judy malware. The good news is that the bad news is wrong. Though this is a malware, there is no question of data leakage. The malware generates unauthorised clicks on the ads to generate revenue to the perpetrators.
Check Point says, "Judy relies on the communication with its Command and Control server (C&C) for its operation. Once a user downloads a malicious app, it silently registers receivers which establish a connection with the C&C server."
In February 2012, Google has improved the security for users from PlayStore with Bouncer. Bouncer is the security platform that scans malware, spyware, trojans and viruses on Google PlayStore. In May 2017, Google has further improved the security with Play Protect. This security layer scans all the apps available on PlayStore on a daily basis.
Though Google is taking care of user security and authenticity of apps available on PlayStore, the perpetrators some how managed to bypass these security layers and could successfully place the "exploit" in PlayStore. It is noted that the malware opens certain URLs and been clicking on ads by running a JavaScript. After thorough research on the point of cause, it is noted that the malware was developed by ENISTUDIO corp. A Korean app development company named Kiniwini hold the rights for ENISTUDIO corp for registering on PlayStore. Though the malware is targeted only on clicking ads, data leakage could be a by-product. Check Point is suggesting the users not to download the apps for just they are available on PlayStore. DO READ the reviews and the check carefully, when the app prompts for permissions.
In Google I/O 2017, Google has stated that globally two million devices are powered by Andoird. The attackers took the advantage of this number and started infecting the Android devices with the Judy malware. The good news is that the bad news is wrong. Though this is a malware, there is no question of data leakage. The malware generates unauthorised clicks on the ads to generate revenue to the perpetrators.
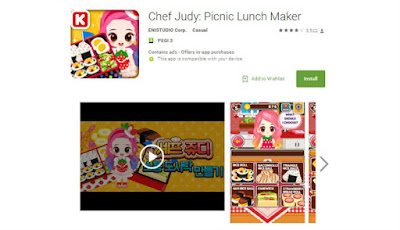 |
| Chef Judy - The Judy malware source |
In February 2012, Google has improved the security for users from PlayStore with Bouncer. Bouncer is the security platform that scans malware, spyware, trojans and viruses on Google PlayStore. In May 2017, Google has further improved the security with Play Protect. This security layer scans all the apps available on PlayStore on a daily basis.
Though Google is taking care of user security and authenticity of apps available on PlayStore, the perpetrators some how managed to bypass these security layers and could successfully place the "exploit" in PlayStore. It is noted that the malware opens certain URLs and been clicking on ads by running a JavaScript. After thorough research on the point of cause, it is noted that the malware was developed by ENISTUDIO corp. A Korean app development company named Kiniwini hold the rights for ENISTUDIO corp for registering on PlayStore. Though the malware is targeted only on clicking ads, data leakage could be a by-product. Check Point is suggesting the users not to download the apps for just they are available on PlayStore. DO READ the reviews and the check carefully, when the app prompts for permissions.









