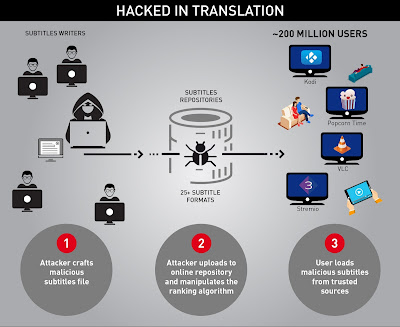
A vulnerability has been figured out in your streaming apps like VLC media player, Kodi and Popcorn-time. As per a research, there are more than 200 million devices using these multimedia streaming apps vulnerable to the attack using subtitles. Basically, we download the subtitles from a website that we find in the Google search results. Hackers are taking advantage of this and framing exploits through the subtitle files. This is one of the easiest ways to get control over a remote system.
With this attack, the attacker may make the user to visit a particular URL or run an inteneded file. We generally do not pay attention while downloading the subtitle files. If you are using anyone of the above applications for multimedia streaming/viewing, take care when you download the subtitle files. Download them only from the trusted repositaries.
We may open a subtitle file and read the subtitles. But, the interesting thing is that there are morethan 25 formats of displaying the subtitles. Each of them provide different capabilities and features. All these media players parse through these subtitle formats and display them on the screen. Normally, the media players are developed in such a way that the default subtitle folder is the same folder where the multimedia file is located. Also, there is no need to seek permission from the user to display the subtitles. Hence, when the user plays the video file, the subtitles are parsed automatically by the media player.
VLC, Kodi, Popcorn Time and Stremio are the media players under the effect of this attack.
Source: blog.checkpoint.com
With this attack, the attacker may make the user to visit a particular URL or run an inteneded file. We generally do not pay attention while downloading the subtitle files. If you are using anyone of the above applications for multimedia streaming/viewing, take care when you download the subtitle files. Download them only from the trusted repositaries.
We may open a subtitle file and read the subtitles. But, the interesting thing is that there are morethan 25 formats of displaying the subtitles. Each of them provide different capabilities and features. All these media players parse through these subtitle formats and display them on the screen. Normally, the media players are developed in such a way that the default subtitle folder is the same folder where the multimedia file is located. Also, there is no need to seek permission from the user to display the subtitles. Hence, when the user plays the video file, the subtitles are parsed automatically by the media player.
VLC, Kodi, Popcorn Time and Stremio are the media players under the effect of this attack.
 |
| Vulnerability in media players with subtitles |









