There has been a stir over the internet with the recent malware attacks from several sources. The Judy malware is targeted on Android smartphones, ransomware targeted on Windows machines and vulnerability has appeared on streaming applications. Almost every major firm announces a bounty for any loophole that is exploitable. Facebook has a Hall of Fame for such bounty hunters.
Millions of devices were affected due to these malware and many more are going to be affected.
The Judy malware is the live example that demonstrates us the degree of vulnerability for a open device connected to the internet. Recently, Google has made its bounty for exploiting the threats in Android devices to $200,000! To provide a secure channel for users, Google runs a security program called Android Security Rewards Program. Here are the details of Android Security Rewards Program by Google to provide the highest level of security possible.
Android Security Rewards Program:
This program is intended to recognise and encourage the security researchers with rewards. Names of the contributors are listed and acknowledged. As of June 2017, This program covers bounties for the vulnerabilities exploited in Pixel and Pixel XL, and Pixel C devices. The amount of bounty depends upon the severity of the vulnerability. The serious the vulnerability, the more the bounty you get. All the bugs explored are listed and your argument is valid only if it is not present in this list. Eligible bugs include those in AOSP (Android Open Source Project) code, OEM code (Original Equipment Manufacturer libraries and drivers), the kernel, and the TrustZone OS and modules. On the other hand, vulnerabilities those are present in the non-Android code are not eligible for the bounty. However, if these vulnerabilities are going to affect the OS or the device security, then these vulnerabilities can be claimed for bounty.
Qualifying vulnerabilities:
Vulnerabilities are qualified into four categories based upon their severity by Google - Critical, High, Moderate and Low severity vulnerabilities.
Rules for rewarding a vulnerability:
- Out of all the requests received, only the first request for a specific bug is considered for reward.
- The report of the bug should be complete i.e., the PoC (Proof of Concept), procedure to reproduce the bug and crash dump if available.
- Bugs those are requested by third-parties are not eligible for the bounty.
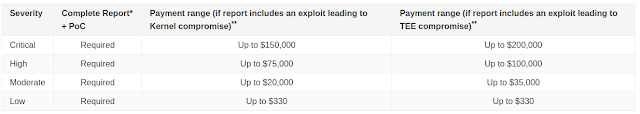 |
| Reward amount for valid bugs w.e.f June 2017 |
The submissions related to patches and CTS are also eligible for the reward, which may be $1,000 each. However, the final amount to be rewarded is decided by the rewards committee of ASRP.
Not all the information security researchers work for money. Google also provides a channel to donate the reward money, if the "bounty hunter" is not interested. The bounties that Google donates are doubled! The rule is that the rewards should be claimed before 12 months of approval. Once, the reward completes 12 months, Google reserves the right to donate the reward to charity.
Here are some of the statistics of Android Security Rewards Program:
 |
| Android bug statistics |
 |
| Rewards for Android Security Rewards Program |










