The security firm Bitdefender has identified another malware into action in the European countries and encrypted data on many of the computers. And now, it has extended to Australia. The Cadbury chocolate manufacturing unit in Tasmania, Australia was shut down due to the cyber attack by the Petya ransomware.
This is the second major attack across the world in past two months, preceded by WannaCry. The WannaCry attack has happened in late April, which was reported by Britain's National Health Service in early May. This attack affected more than 2,50,000 computers across the globe. Just like WannaCry or WannaCrypt, Petya also infects the computers with Microsoft Windows.
What is ransomware?
Ransom means the money paid to do a favour. The same way, post attack, the attackers decrypt the system under attack only after receiving the demanded ransom.
Read more: Judy Chef malware
What happens with ransomware?
When a computer is infected with ransomware, all the files are encrypted, which can be decrypted only by the attacker. The attackers demands ransome for decryption; otherwise the data is lost.
How does Petya ransomware work?
Unlike WannaCry, Petya demands ransom in Bitcoin currency. The exploit for the rasnsomware is called EternalBlue vulnerability of older versions of Windows version. Though Microsoft has released patches to the vulnerabilities, the attack took advantage of the ignorance of the users. The other vulnerability through which Petya can attack is the administrative tools of Windows. The exploit is deployed into a PC by through the links they click.
Read more: Fireball malware
Symantec and Kaspersky claim that their anti-virus applications are capable of detecting the malware through the links which they spread. On the other hand, Microsoft is instructing the users to update their system with the latest patches available from Windows. Though Microsoft froze rolling out updates for Windows XP, official patches are available for a better protection. One of the very basic ways that this ransomware does not affect is through the perfc.dat. If the exploit finds C:\Windows\perf.dat, then the attack is dropped off in the first attempt. Of course, this is NOT complete protection.
What to do if you are attacked by ransomware?
Your computer needs a reboot, in order to encrypt your files and the ransomware needs at least an hour before the PC reboots. When the PC reboots, you can switch off the computer and take care of the data. The following is the screenshot that appears during encryption of your PC data. This is the point where you need to turn off your computer, may be abruptly.
This is the second major attack across the world in past two months, preceded by WannaCry. The WannaCry attack has happened in late April, which was reported by Britain's National Health Service in early May. This attack affected more than 2,50,000 computers across the globe. Just like WannaCry or WannaCrypt, Petya also infects the computers with Microsoft Windows.
What is ransomware?
Ransom means the money paid to do a favour. The same way, post attack, the attackers decrypt the system under attack only after receiving the demanded ransom.
Read more: Judy Chef malware
What happens with ransomware?
When a computer is infected with ransomware, all the files are encrypted, which can be decrypted only by the attacker. The attackers demands ransome for decryption; otherwise the data is lost.
How does Petya ransomware work?
Unlike WannaCry, Petya demands ransom in Bitcoin currency. The exploit for the rasnsomware is called EternalBlue vulnerability of older versions of Windows version. Though Microsoft has released patches to the vulnerabilities, the attack took advantage of the ignorance of the users. The other vulnerability through which Petya can attack is the administrative tools of Windows. The exploit is deployed into a PC by through the links they click.
Read more: Fireball malware
Symantec and Kaspersky claim that their anti-virus applications are capable of detecting the malware through the links which they spread. On the other hand, Microsoft is instructing the users to update their system with the latest patches available from Windows. Though Microsoft froze rolling out updates for Windows XP, official patches are available for a better protection. One of the very basic ways that this ransomware does not affect is through the perfc.dat. If the exploit finds C:\Windows\perf.dat, then the attack is dropped off in the first attempt. Of course, this is NOT complete protection.
Accroding to Ukraininan Cyber Police, the major target of Petya is to get the confidential data from the Ukrain government. Starting from the Europe, the ransomware has spread across US and it's now reached Australia.Read more: Trickbot malware
What to do if you are attacked by ransomware?
Your computer needs a reboot, in order to encrypt your files and the ransomware needs at least an hour before the PC reboots. When the PC reboots, you can switch off the computer and take care of the data. The following is the screenshot that appears during encryption of your PC data. This is the point where you need to turn off your computer, may be abruptly.
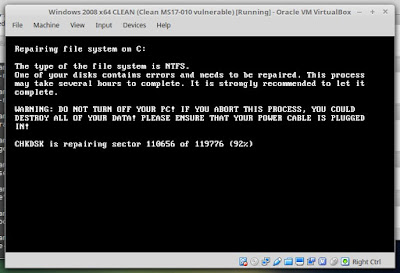 |
| Screenshot of data encryption during reboot |
Beware of the links you click on the internet. More than data source, it has become a source of data breach these days!
Read more: Wanna earn bounty from Google?











0 comments:
Post a Comment