Internet has become part of our life. Just like another aspect, the internet also has both pros and cons - pro being useful to us in every walk of life and con being vulnerable. Starting from WannaCry ransomware, there are several vulnerabilities, malware, ransomware and other security threats has spread across the internet and created a jolt in the spines. This article lists some of the major threats that internet has faced in 2017 till mid-July. The list may be missing some minor threats but covers most of the major ones.
Read more: Most horrible security threats in the history of internet.
WannaCry ransomware:
WannaCry is the first major instance of security breach in the internet in 2017. The attack started on 12th May, and has started infecting more than 2,30,000 Windows PCs across 150 countries. The WannaCry ransomware infects a PC through the vulnerability in Service Message Block (SMB) in Windows OS. Initially, the traces were found in UK's National Health Service (NHS). The attack was highly exposed when US National Security Agency (NSA) used it to create and exploit for its own offensive work, instead of reporting the SMB vulnerability to Microsoft.
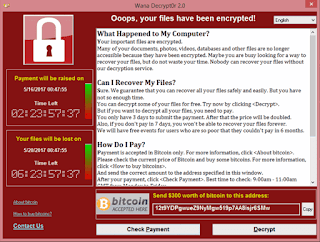 |
| WannaCry ransomware |
Read more: Google bounty has been increased.
When a computer is infected with WannaCry ransomware, the files of the system are encrypted, with the decryption key known only to the attackers. Once the demanded ransom is paid to the attackers, they decrypt the files. The ransom demanded for decryption ranged between $300 and $600 USD. Finally, a 22-year-old information security researcher England has developed the kill switch for the WannaCry ransomware. On this account, Microsoft has released patches to Windows XP also, where the service for Windows XP was halted long back. The loss as of 14th June was expected to be more than $1,31,000 USD.
Read more about WannaCry.
Judy Chef malware:
Judy Chef malware was discovered by the information security agency called Check Point. The malware was found on the Google's official app store Google Play. More than a malware, Judy Chef is an adware - it click on the links that generates ad revenue to the attackers. After a thorough research, the researchers found that the malware was found on 41 apps available in the Google PlayStore. The malware has infected more than 4.5 million devices, which was downloaded more than 18.5 million times. Some of the apps were found out to be on Google PlayStore for years.
 |
| Judy Chef malware |
Judy Chef malware relies on the communication with its Command and Control server (C&C) to obtain the database of the ad URLs. The malware downloads the target URLs from C&C server and generates clicks on the links without the knowledge of the user, which leads to the generation of ad revenue to the attackers. With the report of Check Point to Google, Google has inspected and removed all the apps with the malware.
Read more about Judy Chef.
Fireball malware:
Check Point, again, play the key role in discovering the Fireball malware. The Fireball malware manipulates the web traffic and generates ad revenue to the attacker just like Judy Chef. The activity of Fireball is very high when compared to that of Judy Chef. The malware installs arbitrary files and plugins that generates the ad revenue. The origin of this malware was found in a Chinese marketing company called Rafotech. The malware is bundled along with a software that a user downloads from the internet.
The malware reciprocates itself with a process that seem legitimate running. Once the system is infected, the malware starts its activity - clicking on the target URLs and downloading the target plugins for generating the ad revenue. More than 25 millions of PCs were infected with Fireball malware only in India.
Read more about Fireball.
Trickbot malware:
The Trickbot malware is a serious threat to the victims. The malware was developed to tap the bank-related details of the user. When infected, the link a user clicks undergoes a series of redirections, where the page navigation seems legitimate but finally leads to tapping of sensitive data from user, without the knowledge of the user.
The malware was found to be developed mainly targeting the banks SBI and ICICI across India. There are several speculations that many other banks may be included in the list. However, there is no activity of the malware till date. The internet security solution provider eScan discovered the malware and claims that the activity may appear in coming weeks.
Read more about Trickbot.
Cyber attacks on Westminster square:
This attack was completely regional and restricted to the Westminster square in the UK. The attack halted the access to the e-mails of the MPs and other officials of Westminster square. As soon as the report reached the information security team of the Westminster estate, the issue was resolved in collaboration with the National Crime Agency (NCA). However, there are speculations that there was loss of sensitive data related to administration, very latter to the attack. There is no official confirmation on this.
Read more about Cyber attacks on Westminster square.
Petya ransomware:
Though the Petya ransomware was discovered in 2016, it has spread effectively towards the end of June. This is very similar to the WannaCry ransomware and spreads with the similar vulnerabilities. WannaCry encrypts all the files available on the system but, Petya ransomware encrypts the master boot record of the OS, encrypting the Master file table of the the Windows' NTFS file system upon restart. Another difference is that the ransom for Petya is to be paid in bitcoin currency.
The ransomware is propagated through the mail attachments. Though the attack was initially targeted Ukraine, the attack has spread across the globe. As a result of this attack, the Cadbury factory in Australia was shut down and the radiation monitoring system at Chernobyl Nuclear Power Plant was also halted. Several other firms like Saint-Gobian and DLA Piper were also affected by this attack.
Read more about Petya ransomware.
Copycat malware:
The Copycat malware infected the devices powered by Android across the globe. The malware was discovered by Check Point and it was estimated that more than 14 million Android devices were infected with the malware, out of which more than 8 million devices were successfully rooted. The Copycat malware infects through the URLs that the user clicks. Zygote is the daemon process that is responsible for application launch in Android devices.
Read more: Four ways to stay protected from ransomware.
Once a device is infected with Copycat malware, it attaches to the Zygote process and restricts the access to all the applications that Zygote handles. Copycat is the combination of adware and malware. Along with tapping the sensitive user data, Copycat also clicks on the target revenue generating URLs. This is what the information security researchers call being state-of-art.
Read more about Copycat malware.














0 comments:
Post a Comment